REMOVING MALWARE
To deal with viruses and spyware or malware can be very difficult, even a showstopper. This depends on how bad the malware is and how deeply embedded into the system it has become. There are times when if caught very early some malware can be eliminated but it often means some complexity of work. If you have a machine that is currently infected with malware such as what has just been mentioned, there are a few things that you can try to eliminate it. It is doubtful that you are using that machine right now, because most of these instances of malicious code will stop you from even using your Internet browser; however, you can use this information to go back to that infected machine and make some serious attempts to resolve the situation. If you do not already have good anti-spyware/malware and registry cleaner installed on that machine get them now (download from another machine and place on cd/dvd/usb if need be) because you're going to need them even if you are not able to fix the currently infected machine right now.
If you see an indication of a malware infection, the best bet would be to SHUT THE COMPUTER OFF immediately (hold the power button in for 5-10 seconds until it shuts off). There are a few notable procedures to try in order to KILL this thing whether or not you have good Anti-Malware software currently installed, but we hope that in any case a wipe/recovery can be avoided (Please bear in mind that this will not always be possible – but we will go over the best way to recover if need be saving as much in the way of saved data as possible). Some of this might be considered time-consuming, but if one wants to save what is on their hard drive these procedures may well be worth trying.
If you do have good anti malware already installed, the infection will first attempt to stop you from using it; therefore, one possibility is to try renaming the installed anti-malware program to "Explorer.exe". The malware is not likely to prevent Explorer.exe from running therefore you may be able to run MalwareBytes or any other installed program you have renamed. Sometimes this actually works and will allow you to remove the malware infection. There are even some cases where you may be able to move the window being displayed by the malware out of the way so that you can activate your installed software. This is quite simply not always possible but worth trying. Failing the above it makes sense to move on to a few more procedures to kill this infection.
If your machine is off, turn it on and hit F8 repeatedly; if the machine is already on, try reboot and hit F8 repeatedly. This should give you the option to start the machine in Safe Mode with Networking. Once the machine has booted into Safe Mode with Networking the idea now would be to kill the process with which the malware infection is running. To do this you must identify the actual process and that should not be difficult. While in safe mode there are fewer processes running than under a normal boot condition, and with a shorter list it should be relatively easy to spot the infection’s process.Take a look at what processes are running by opening a DOS prompt which can be done by hitting the Windows key + R to open the run box, type CMD and at the flashing cursor type tasklist. Now you will see all the processes that are running with their image names and their process IDs. Now check the Start Menu and All Programs for unknown programs (like what was displayed) and compare to the tasklist. See anything “funny” or wrong?
Note: Do NOT under any circumstances kill a process that is legitimate. (i.e. do as I say not as I do; and -- some infections will appear as legitimate processes) Such action can cause system instability and/or worse!
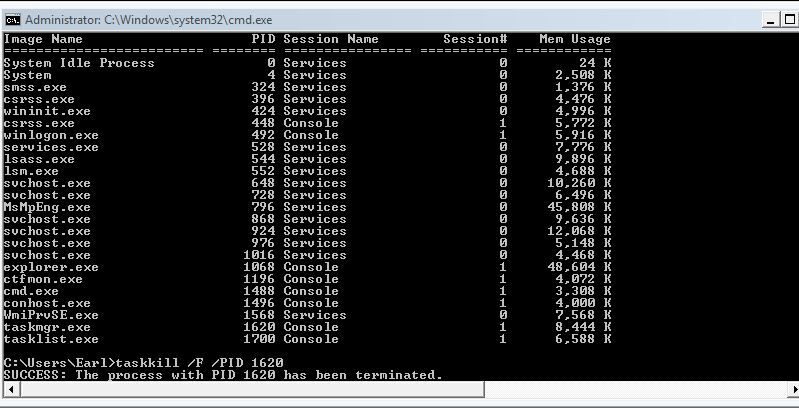
The above image displays the command prompt (or DOS prompt) window after I had done the above; beyond that, it also shows all totally legitimate processes and how I force - killed one of them. The process I killed in this case was the task manager that was running at the time. The process you are looking for will be none of what is displayed above but something more like is2010.exe or xp2012.exe depending on what your infection's name is and it will likely be the same or similar to what you had seen displayed on your screen. Therefore, once you know the process you can force - kill it (and it’s child processes) in that same command prompt window by typing taskkill /f /t/pid 0000 (the number next to the infection’s name). It is also possible to use the “image name” by typing taskkill /f / t/im xp2010.exe (whatever the exact process name is). In any case, if you see that the rogue process has been terminated, you can run your installed anti-malware program (full scan) followed by running a good registry cleaner like CCleaner or proceed below if you don’t have any installed. Do NOT reboot the computer at this time unless you have seen that your installed software has successfully cleaned the system.
