Cryptolocker Ransomware
Ransomware is something that's been around for quite some time. According to Wikipedia the first known instance occurred in 1989, known as PC Cyborg (aka the AIDS Trojan). That piece of malware encrypted files on a hard drive, proclaimed that there was an expired software license on the infected system, and demanded payment to resolve the falsified situation. One of the latest instances in the wild is called Cryptolocker and it is capable of some very nasty activity. Cryptolocker Ransomware is far more complex and potentially damaging than any of its early predecessors but it can be dealt with if one knows what to do about it.
What is Cryptolocker?
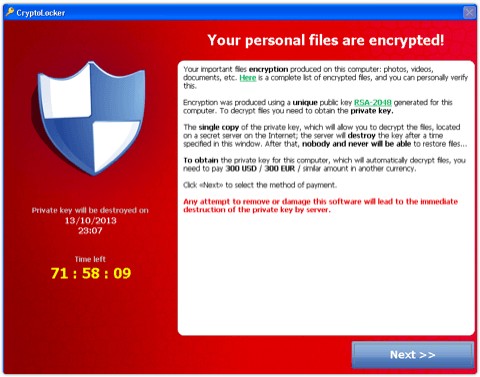
Cryptolocker is a complex piece of malware which contains a virus hidden within a phishing message attachment (or injected just by visiting an infected website) that has all the appearances of coming from a legitimate source. If one is fooled into opening the attachment, Cryptolocker will then execute and begin encrypting any files with a number of file extensions that it targets on the host computer. This includes all forms of Office Documents and many other file types so that once they are encrypted the user has access to very few of their files. Currently Cryptolocker targets Enterprise Windows OS distributions as opposed to randomly targeting the PCs of the general public, and spreads only to local or mapped drives, but this does not mean that it will not evolve into something that will threaten a broader segment of cyberspace.
Once Cryptolocker gets into a system and encrypts all the files it has targeted, this Ransomware then demands payment to decrypt the files so that the user can once again access them. The files are encrypted using a (reportedly near unbreakable) public-key installed on the host computer and a private key which is stored on Cryptolocker’s server and according to the author’s threats that private key will be deleted in a matter of days if payment is not received to decrypt the files. This would make it extremely difficult to retrieve these encrypted files in many circumstances. There are however ways in which they can be recovered depending on how the operating system is configured.
Fixing Cryptolocker Encryption
Because Cryptolocker's encryption has yet to be broken the best way to fix the problem is to restore the system from a backup. In other words Cryptolocker cannot literally be “fixed” at this time. Even though security software can remove the Cryptolocker Ransomware, it cannot decrypt what has been encrypted. If you have system restore enabled (a.k.a. system protection depending on your OS) then you should have available the option to restore previous versions of files and folders. If you right-click on a file or folder, choose properties and see that there is a previous versions tab you can click on that to restore a previous and hopefully unencrypted version of that file or folder.
Some have actually paid the ransom to get there Cryptolocker encrypted files decrypted, but if there are other options that would obviously be a better thing than paying a criminal to solve a problem created by a criminal. There may never have been a better reason to create a backup so if you have not please do so now. If you're not sure how to do that you can find out how to make a backup at Resolve here. It is also advisable to keep system restore/protection enabled (as it is by default) so that you do have previous versions available to you. There are ways to also prevent the infection of malware such as Cryptolocker and that will be covered soon in Resolve’s Security section. If you have any questions regarding this please don’t hesitate to register and ask in the Forums, and/or use the contact form found here.
